Securing SQL Server: Renaming and Disabling the SA Account

The SA (System Administrator) account is a predefined account in SQL Server that has full control over the database server. By default, the SA account is disabled and is not associated with a login. However, if the SA account is enabled and given a password, it can be used to connect to the database server and perform any task.
There are several reasons why you should consider renaming and disabling the SA account for security purposes:
The SA account is a known account: The SA account is a well-known account that is present in every SQL Server installation. As a result, it is more likely to be targeted by attackers. By renaming the SA account, you can make it more difficult for attackers to identify and target this account.
The SA account has full privileges: The SA account has full privileges on the database server, which means that it can perform any task. This includes tasks such as creating new logins, modifying database schema, and backing up and restoring databases. If the SA account is compromised, it could be used to perform malicious activities on the database server.
The SA account is a single point of failure: If the SA account is compromised, it could be used to gain access to all of the databases on the server. This could result in a significant data loss or breach. By renaming the SA account, you can reduce the risk of a single point of failure.
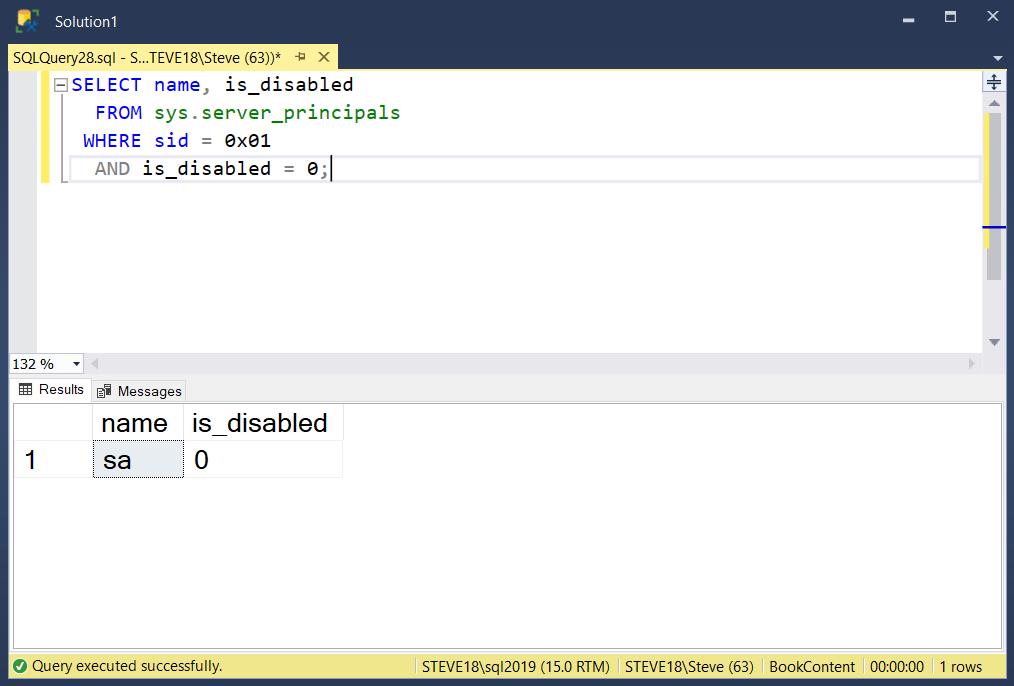
Here is a query to check the SA account, the recommendation is that when this query is run that it would not return SA in the first column, and that it would return 1 in the second column.
SELECT name, is_disabled
FROM sys.server_principals
WHERE sid = 0x01
AND is_disabled = 0;
Of course before you go and disable and rename your SA account, you will want to be sure that at least one other user has the same permissions that SA would have so that you are not locked out on certain features.
Renaming the SA account can help to improve the security of your SQL Server installation by making it more difficult for attackers to identify and target this account. It is a best practice to rename the SA account and use other, more secure accounts for tasks that require administrative privileges.
Want to learn more about securing your SQL Server, take a look at my free white paper on sever steps to help harden your SQL Server.
Securing SQL Server Whitepaper.
More from Stedman Solutions:
Steve and the team at Stedman Solutions are here for all your SQL Server needs.
Contact us today for your free 30 minute consultation..
We are ready to help!

I still wonder if renaming the account has any benefit.
We all know that the sid 0x01 = sa and usually if you have managed to gain access to a system with another account (sa is disabled) that has access to create logins or reset passwords then renaming the account added no benefit that I can think of.
Unless there is something performance / risk related on how SQL responds to an auth request when looking at “login not found” or “Account is disabled” I could not see a reason.