Week 2 Challenge Details
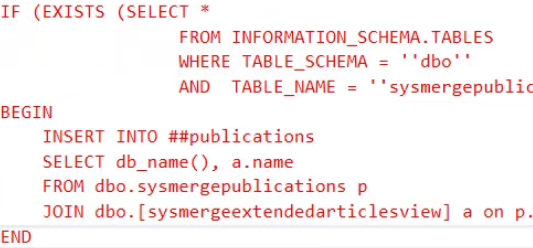
Week 2 Challenge: You can download a zip file with multiple backup files created on SQL Server 2008 that can be restored and used on SQL 2008, SQL Server 2008R2, SQL Server 2012 or SQL Server 2014. The story… A backup was run yesterday, after that backup several changes were made to the database, inserts deletes, updates, and more. Sometime …